Lock the Front Door: Smarter Cybersecurity Moves for Small Businesses

You wouldn’t leave your storefront wide open overnight. So why do so many small businesses leave the digital lights on, doors unlocked, and passwords taped to monitors like it’s still 2005? The truth is, cyber threats aren’t just a big business problem. Hackers know that most small businesses don’t have robust protections in place, which […]
AI in Cybersecurity: What’s Really Changing (And What’s Not)

How long before our entanglement with AI turns toxic? Take Snapchat’s ai knowing where you are when your location is off. Those eerily accurate targeted ads that make you wonder if your phone’s listening. Or how “Is AI going to take over [insert industry]” headlines are popping up every day. Reality check: The same AI […]
Blue Yonder Today, You Tomorrow?

There’s always something going on in the cybersecurity space. Today, It’s a ransomware attack on Blue Yonder, a leading supply chain management software provider. Tomorrow, and trust me I hate to put it this way, but it could be you. The Far-Reaching Consequences of Cyberattacks On November 21, Blue Yonder reported disruptions in its […]
Optimizing Network Performance and Security for IT Infrastructure
Molaprise enhanced network performance and security for a client by utilizing SolarWinds tools for monitoring, analysis, and troubleshooting, ensuring accurate data collection, security compliance, and efficient device configuration management.
The Most Recommended Password Managers According to Reddit
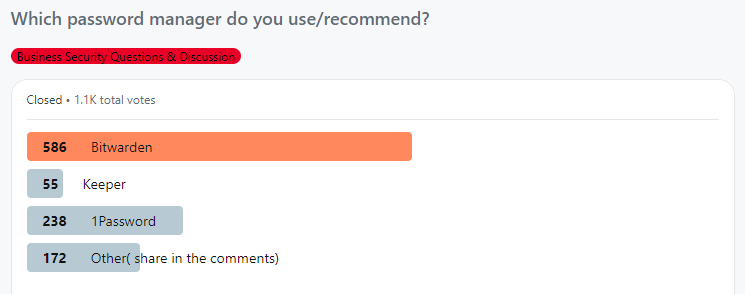
Having to memorize multiple passwords for different sites is the kind of stress nobody has time for. We’re constantly reminded of the importance of strong, unique passwords, but to be honest, many of us struggle to remember and manage them effectively. Reusing passwords is simply convenient and besides, there’s always the “Forgot password” option that […]
CrowdStrike’s Bug Fix: What You Need to Know About the Latest Update

We’re back with the latest on the CrowdStrike issue. CrowdStrike recently released an elaborate 12-page report titled the Channel file 291 Incident Root Cause Analysis. Today we’re breaking down this technical document into simple terms starting with a quick rundown of events. On July 19, 2024, CrowdStrike discovered a bug in their security software that […]
Think Before You Click: Identifying Phishing 101

If you haven’t been socially engineered at least once, you might have been and just didn’t realize it. Social Engineering is a manipulation tactic used to trick targets into performing specific actions or divulging sensitive information. Rather than targeting technological vulnerabilities or using brute force attacks, this technique targets YOU – the human element. A […]
The CrowdStrike Falcon Sensor Outage: Preparing for the Unexpected
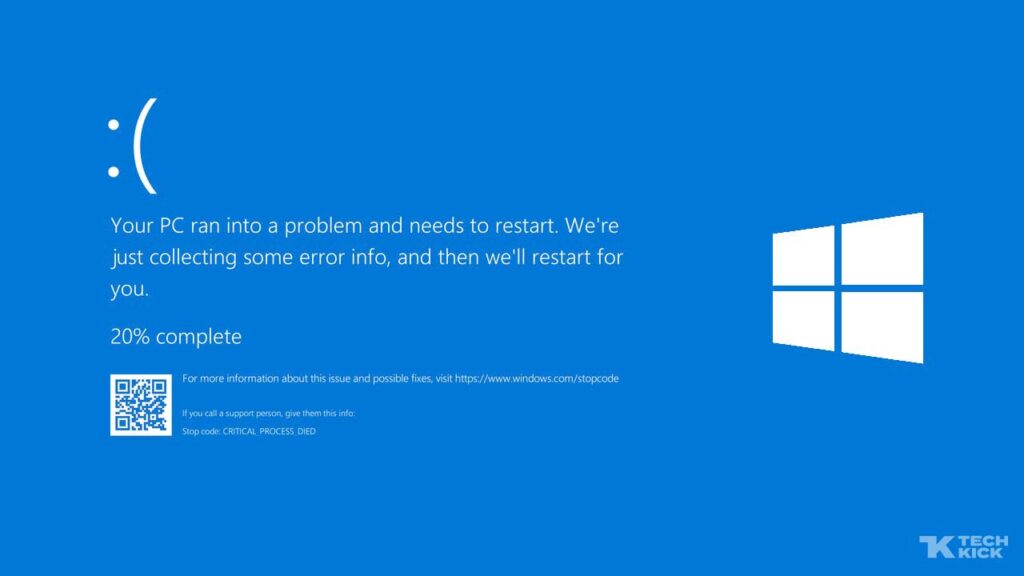
If you ever wondered what a cyber apocalypse would look like, the recent CrowdStrike Falcon Sensor outage might’ve given you a glimpse. Categorized as a software defect and not a malicious cyberattack, the IT outage involving CrowdStrike’s Falcon Sensor software was caused by a defect in a content update specifically affecting Windows hosts. This led […]
Understanding Smishing Attacks
Ever gotten a “STOP” to unsubscribe text? That may have been smishing bait to identify active phone numbers. Smishing (SMS + phishing) is a common cybersecurity threat in which attackers use text messages to trick people into disclosing sensitive information. This attack exploits our mobile habits, luring us into trusting seemingly familiar numbers amidst the […]
Why Your Business Needs an IT Infrastructure Upgrade

In the relentless pursuit of success, businesses stand at a crossroads where the choice between progression and stagnation becomes clear – the state of your infrastructure. Why is clinging to outdated infrastructure no longer an option? Let’s discuss the pitfalls, challenges, and missed opportunities that come with relying on yesterday’s technology.
